Background
As if this year has not brought enough turmoil and chaos to the country and world, this hack shows that 2020 had at least one more trick up its sleeve. In case you have not heard already attackers were successful in inserting a trojan into a widely used enterprise IT management called Orion from the software company SolarWinds. We may never know the full scope of this hack but any company that installed or updated Orion in the last 6-9 months is potentially at risk. It is very likely before this week you have never heard of Solar Winds so how bad can this be? Solar Winds has a large customer base as shown by the screen capture below from their now removed webpage.

How Widespread is it?
It is estimated over 18,000 entities used SolarWinds Orion product suite. Over the next days, weeks, and months you will probably hear of more and more companies and government bodies that have been breached. This hack has affected local governments from Pima County to highly sensitive Federal government agencies such as the Department of Energy’s National Nuclear Security Administration as well as the U.S. Treasury and Commerce departments. Several organizations such as Cox Communications, Microsoft, Ford, and many others have been affected.
How bad is it?
The attackers were not out to cause chaos and destruction, that would have been a waste of their efforts that would have brought this hack to light very quickly limiting its effectiveness. Rather they built some intelligence into the trojan such as not executing until several weeks after installed. They took efforts to make sure the files were signed and trusted like all other SolarWinds software. The trojan’s communication with the hackers was disguised to look like the SolarWinds traffic in order to obfuscate it and prevent detection. This hack was probably months or years in the making and there is currently no information on how it was accomplished. Some of the likely ways were; directly hacking into SolarWinds systems, using reused credentials, or paid an employee to help with the attack. It was most likely a nation-state actor such as agents of the Russian government from the current indicators.
Is my company at risk?
From what is currently known, only companies that had SolarWinds Orion with specific versions are affected. Orion is a product that is typically only used by larger companies as it is very expensive and is used to manage large computer networks. If you did not have this product installed on your network you are not at direct risk from this attack, most likely you did not. Any company that does or did have this product installed in the last year should immediately take steps to investigate, remediate and recover. Luckily Microsoft and others have taken steps to take down the command-and-control network used by the attackers, but that does not mean they did not get alternate access to breached networks and time is of the essence in situations like this.
Even without the product installed you and your organization can still be at risk. The highest risk will be from your information being used by the attackers. Being they accessed companies, ISP’s, hospitals and government agencies any sensitive information they had could be out in the wild. There is little to no direct risk to you or your organization from being hacked through any of these vectors. Except for in very care cases, your ISP such a Cox Communications being breached, did not and does not give the attackers inside access into your networks. Most businesses use a router/firewall which is not managed by Cox or other ISP’s and would make their network being breached no different than any other internet attack against your company.
With that said the attackers wanted high value targets and would not have had the resources or want to risk their efforts being caught by going after what would be a low value target to them. Government agencies, large companies, defense contractors, hospitals, Universities and ISP’s are their most valuable targets.
What now?
If your organization uses or recently used Orion, I hope you are not still reading this and have already contacted your IT department, Lawyers and a good cybersecurity incident response company such as Cynet, FireEye (yes that is another story in itself), CrowdStrike, SecureWorks or others.
For the rest of us the best thing we can do is take steps to increase our security posture. It is not possible to stop all threats but good cybersecurity hygiene and best practices will protect us from most attacks reducing the likelihood of a breach. Many organizations already have compliance standards they might need to follow based on their industry, such as HIPAA for health care providers, PCI for retail businesses, NIST 800-171 for Department of Defense contractors, SOX for publicly traded companies, Gramm-Leach-Bliley Act for financial institutions, just to name a few.
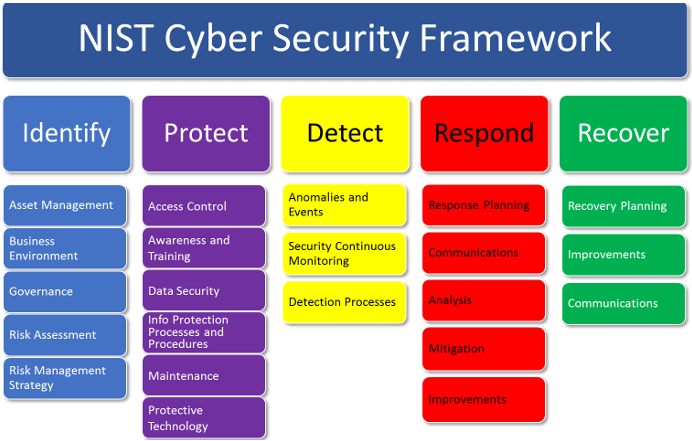
For companies that do not fall in any of the mentioned regulations, the NIST Cybersecurity Framework is a good starting point for processes and procedures to harden and company against cyber-attacks. This framework is a scaled down version of the NIST SP800-53 which is cost prohibitive for most small companies. The CSF has guidelines to help a company Identify, Protect, Detect, Respond and Recover as shown in the graphic below.
Final Thoughts
Cybersecurity is more than just implementing technological safeguards. It is technology along with ongoing administration and processes with the goal of reducing risk. This will require some internal change and, in most cases have financial costs associated with it. The cost of not taking steps to protect the organization could be much higher in the terms of reputation, loss of business, government fines or lawsuits.